I’m sure most people are familiar with aquariums, salt or fresh water containers filled with flora and fauna plus various components to keep the aquarium alive: heaters, pumps for aeration and filtration, light, pH controllers and more. An aquarium is a system. Those components are various controls to keep the system in balance (e.g. temperature, Oxygen, pH, Nitrogen). Even some fish and plants play a role in recycling and cleaning, as anybody who had added a bottom feeding catfish to “control” the detritus knows. All of these are system controls, working within the system to manage and maintain it.
Of course, there are other controls outside of the system. A light bulb goes out, a responsible party replaces it. The utility company provides electricity to the various electronic components, which is wholly outside the system of the “aquarium.” When the system gets out of whack (e.g. an algae bloom), it may require disassembling, cleaning and reassembling to get it back into balance. These controls, called environmental controls, outside the boundary of the aquarium system, monitors the system and inputs and potentially rebuilds the system, altering, adding, replacing or subtracting inputs or components. Sometimes determining the boundaries of the system can be difficult, but it can be important when building a system to figure out what needs to be managed within the system and what the system needs to rely on, externally, being managed. Often, the environment is just a much larger system (e.g. a local ecosystem is part of the Earth’s ecosystem which is part of the Earth/Moon system, which is part of the Solar System, etc…)
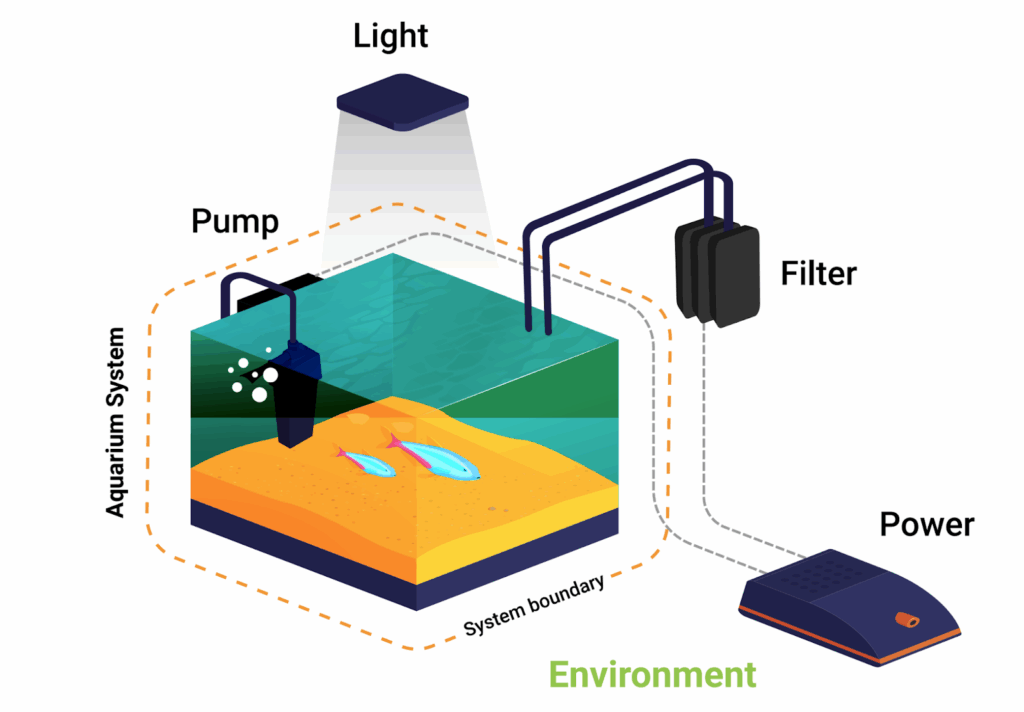
In privacy and security, controls are often broken down into technical and administrative categories. While helpful, this labeling often obfuscates the system/environment distinction. While many technical controls may be within the system and many administrative controls manage the environment, the relationship is not one of equivalence. Returning to the aquarium, a battery backup could provide power during intermittent outages. This seems a technical control, but also seems external to the “aquarium” managing the environment in which the aquarium operates, to ensure it has electricity. Manually checking the pH and adding chemicals to balance it may seem ministerial and external, but as part of the normal operations of the aquarium, it is part of the aquarium system. The definition of a system is apropos here: “a group of interacting, interrelated, or interdependent elements forming a complex whole.” System boundaries are not necessarily physical and may be tied to what one considers “part of the system.” Take the battery backup. If the aquarium was solar powered, that power source and the backup could be defined as part of the aquarium system. The fundamental question is whether the responsibility lies within the system or outside. Is it the responsibility of the system operator to provide (i.e. the aquarist maintains the power source) or a different party (i.e. the power company).
The reason we care about distinguishing system versus environmental controls is that when doing design (i.e. “privacy by design”), we can build in system controls but don’t necessarily control the environment in which the system operates. Of course, this gets muddled when talking about services or business processes where the designer may also influence the environment, sometimes significantly. I find the best way to approach this is to picture, simplistically, the system being designed as self contained, a product to be sold on a shelf (e.g. a closed ecosystem aquarium). Even for more complex services, you can imagine another company acquiring the service. What would you sell them versus what are integral parts of your business that wouldn’t be part of the acquisition? Would you sell them your data center and its power supplies, security cameras and fire suppression equipment? Would you sell them your privacy policy and employee training, which forbids them from accessing certain data?
For privacy and in the context of information technology, I advise people to think about the controls you’d put into an IOT device that had no back-end services: controls that limit collection of information or reduce interactions, controls that minimize data, controls that prevent sharing. These are the system controls. Controls like risk assessments (which include privacy impact assessments), code audits, policies, usage restrictions and the like, would be environmental controls. They affect the design of the IOT device or the world in which the device operates, but they are not contained within the device.
The IOPD Standards Committee is currently engaged in developing a controls catalog with a focus on system controls that can be built into the system, be they technical or administrative. While developing the Design Assurance Standard, the committee found a profound lack of these types of controls. Most controls were focused on the environment, or external controls. In NIST 800-53 rev 5, Appendix C, controls are distinguished between system controls (“S”) and organizational controls (“O”), with some controls implemented in both domains. System/organizational is closer to the technical/administrative distinction than our system/environmental bifurcation (i.e. “A control or control enhancement that is typically implemented by an information system through technical means is indicated by an “S” in the implemented column.”). That being the case, that most privacy controls fall in the organizational categorization is telling. There is a lack of privacy-specific system controls. For clarity, privacy-specific controls are those that mitigate privacy risk (i.e. the likelihood or severity of some event that impacts a person in a way that is generally regarded as falling under the umbrella of “privacy”).
As organizations are looking to apply the Design Assurance Standard, it’s imperative upon them to identify and implement controls within the system they are designing and not simply rely on organizational or administrative controls that may not be persistently available. We hope the privacy controls catalog, which should be published sometime in 2026, will be helpful in that regard.
For previews, drafts, and to get involved, consider joining the IOPD as an Individual Ambassador!
Postscript
One may wonder where a “user” of a system is situated. It all depends on their role. Consider a webserver serving up webpages. A user could be the designer setting up a web page. They could be a visitor logging into their account on a website. All of these are perfectly situated within the confines of the web serving system. While a server admin would easily be considered a part of the environment, they wouldn’t be considered a part of the web serving system, they are controlling the environment (how much RAM the system has, what kind of Internet connection, etc.) What about a web admin who configures the server? This is where it gets tricky. Doing routine tasks like adding web pages, deleting spam, may fall within what we consider the web server system. Other tasks, like adding plugins for additional functionality, are changing the system. The user, in this case, is part of the Environment, altering the system from the outside.

